AI and Crypto – A Dangerous Combination of Cloned Voices and Cybercrime Threats
Cloned voices are becoming a serious risk in cryptocurrency, allowing hackers to impersonate trusted individuals and steal digital assets. Stronger security measures are essential to combat this emerging threat.
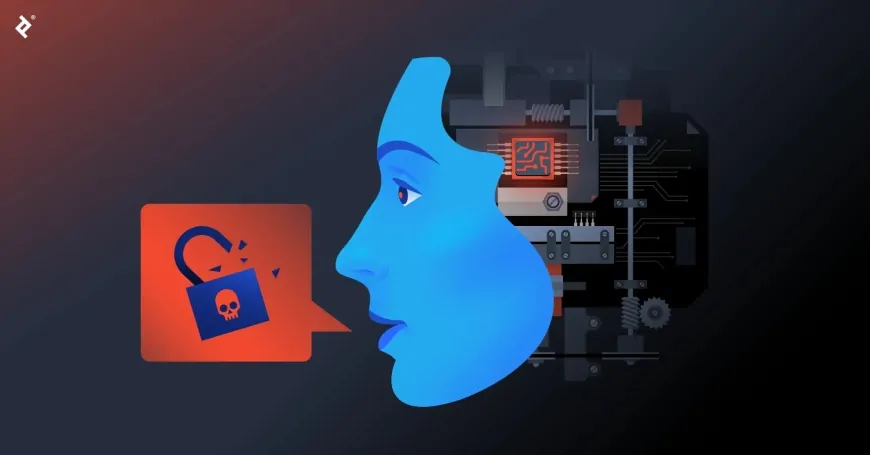
Imagine this: you’re going about your day, maybe checking in on a friend or responding to a colleague through a voice message. Suddenly, you hear a voice you know and trust asking you to send a cryptocurrency payment. But here's the twist—it’s not actually them. It’s a cloned version of their voice, created by hackers. This might sound like a scene out of a thriller, but it’s quickly becoming a reality as technology advances.
In this piece, we dive into the risks of voice cloning and its connection to cryptocurrency, exploring how everyday communication tools are being weaponized and why it’s time to rethink our approach to cybersecurity.
Voice Messages: A Convenient Tool, But Not Without Risk
Voice messages are something most of us use daily, whether it’s sending a quick update to a friend or discussing a project with a coworker. First introduced on WhatsApp in 2013, voice messages quickly became one of the most popular features, with over 7 billion sent every day by 2022. Many people prefer voice messages because they convey emotion and tone much better than text, making conversations feel more personal and genuine. In fact, studies show that 61% of people find it easier to understand tone in voice notes, and half of users feel closer to their loved ones thanks to them.
But while voice messages have improved how we stay connected, they’ve also made us more vulnerable. As voice cloning technology improves, hackers now have the ability to replicate someone’s voice with startling accuracy. And this is where things get dangerous.
The Growing Risk of Voice Cloning in Cryptocurrency
The increasing sophistication of voice cloning tools has raised alarms, particularly in the world of cryptocurrency. Hackers can now collect voice samples from public sources like social media or old voice messages, using them to impersonate individuals. This is especially concerning as more crypto platforms adopt voice-based security measures, such as voice authentication, to protect user accounts.
Imagine this: a hacker impersonates someone you trust, like a colleague or family member, and asks you to transfer cryptocurrency to a wallet. Because the voice sounds so convincing, it’s easy to be fooled. Security experts point out that this kind of scam is harder to detect than traditional phishing attacks, making it a serious concern for those dealing with digital assets.
Grace Dees, a cybersecurity analyst, warns that voice cloning is a game-changer for fraudsters. "Using cloned voices in phishing attacks significantly boosts their success rate," she explains. "It’s a new level of deception, and it’s much harder to spot."
Voice Cloning’s Broader Impact
The issue doesn’t stop at cryptocurrency. As voice-controlled devices become more common in homes, workplaces, and healthcare settings, the risks of cloned voices extend far beyond digital wallets. A hacker with access to a cloned voice could manipulate voice-activated systems—disabling security features, altering device settings, or even accessing sensitive medical equipment.
As we rely more on voice technology, trust becomes a key concern. If people begin to feel that voice-based systems aren’t secure, it could slow down innovation in industries that depend on this technology. The challenge, however, lies in the difficulty of investigating these crimes. With voice cloning becoming increasingly hard to distinguish from real voices, it’s tough to track down and prosecute those responsible.
What We Can Do to Stay Protected
Voice technology is personal—it’s how we connect, share emotions, and trust each other. But if it’s being used against us, it changes the game entirely. So how do we protect ourselves in this new landscape?
First and foremost, it’s important to invest in better security systems that can recognize and block synthetic voices. Being cautious about the amount of personal voice data shared online is also key. The less data hackers have to work with, the harder it becomes for them to exploit it.
As technology continues to evolve, our approach to security needs to evolve with it. Whether we’re using voice-activated devices or sending cryptocurrency payments, staying informed and vigilant is our best defense against the growing threat of cloned voices.
Also Read: Instagram and X Launch New Video Tools as TikTok Faces Ban